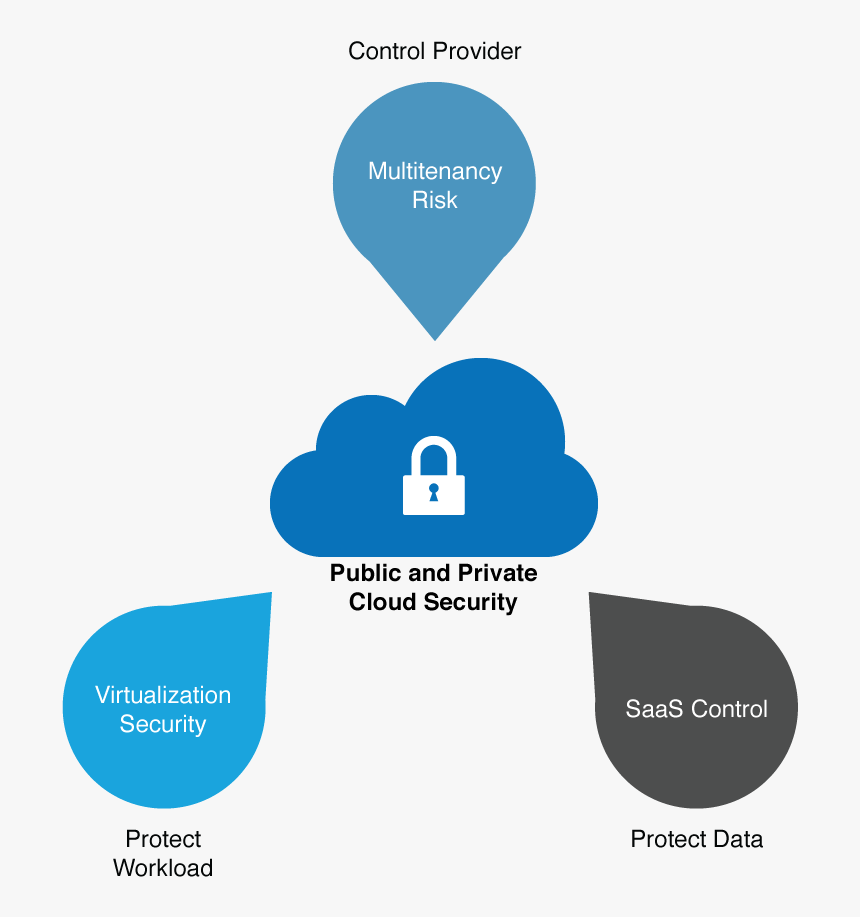
We are leaders in Cyber Security Advisory Services and providing Cyber Security Services for over 20 years. Having exposure across all the Cyber Security Services and align the Security of your technology with business and provide security keeping in mind confidentiality, integrity, and availability of data. We offer a multitude of Cyber Security Services to enable fast-paced agile environments are secured through the development life cycle.
Cyber Security Risk Management Framework, most of these focus on identifying risks, assessing these risks, apply mitigating controls, and manage residual risks. Depending on the type of industries and geography we will work on developing and implementing a risk management framework. ISO 27000, NIST, or any other Cyber Security Risk Management framework of your choice. We have been actively involved in this process for over two decades and we ensure our clients and driven to success and establish a complete end-to-end risk management framework that is self-drive and repetitive and able to pass any internal and external compliance assessments.


VCISO – Chief Information Security Officer
Depending on the need and size of the enterprise we are in a position to cater to your needs of a Virtual Chief Information Security Officer to ensure all of your Governance, Risk Management, Cyber Security, and Compliance needs are met at the fraction of the cost.
VBISO – Business Information Security Officer
BISO is the leader who is aware of technology and business. A BISO will bridge the gap between Technology and Business leadership to ensure both these are aligned to deliver security and success to the management.
Data critical fuel in the information age, depending on the type of business we need to safeguard data and inform its owners if there is a breach. Across the globe Data Privacy and compliance laws have been formulated with the sole purpose of them to ensure data is not misused and appropriate measures are put in place to identify critical data elements and apply relevant controls to safeguard. The rigor of compliance varies depending on the type of industry such as banking, healthcare, government, and telecom, automobile type of data like health, personal, or payment data. Privacy Compliance such as GDPR, CCPA, LGPD, India Personal Data Protection Bill, Chile Privacy Bill Initiative, and New Zealand Privacy Bill.

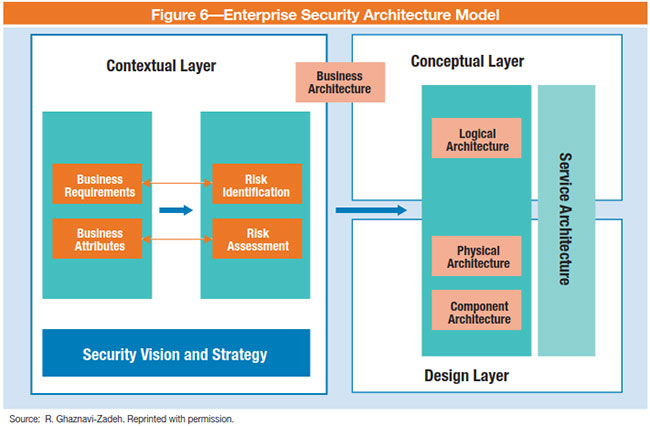
Enterprise Security Architecture meets the business needs and takes care of ever-changing security threats and ensures the business is not impacted by any adverse security events. Our team can align your technology architecture with business needs and ensure key preventive, detective, corrective, and directive controls as applicable. Depending on the type of enterprise need we can provide security architecture services using SABSA and TOGAF.
Every business has critical information or data to protect. Depending on the type of business security strategy is defined to meet your expected goals to protect information – the measures vary depending on whether you are a bank, hospital, credit card company, automobile or travel and tourism or oil and natural gas company. Identifying regulatory compliance needs and security framework meets these regulatory requirements.

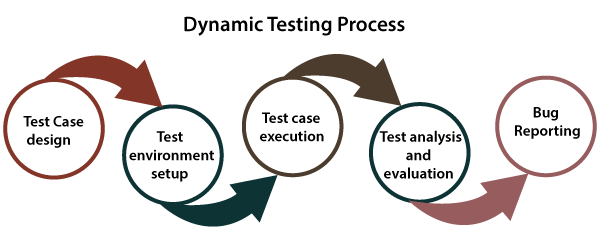
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.

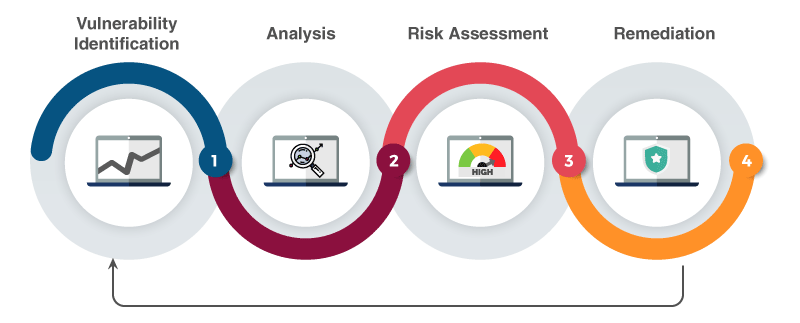
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.