Cyber Security Risk Management: We can partner with you to deliver best in class cyber security risk management function for your organization. Having worked in IT and Cloud and done numerous projects on Cyber Security Risk Assessments and identifying critical gaps affecting the enterprise. Depending on the compliance needs we can tailor the risk management function to better suite your cyber security needs.
Depending on the type of industries and geography we will work on developing and implementing a risk management framework and we will run the risk management program for you. ISO 27000, NIST, or any other Cyber Security Risk Management framework of your choice. We have been actively involved in this process for over two decades and we ensure our clients and driven to success and establish a complete end-to-end risk management framework that is self-drive and repetitive and able to pass any internal and external compliance assessments.

Is a type of Testing performed to identify vulnerabilities, threats, risks in a software application to prevent malicious attacks from internal/external threat actors. The purpose of such testing is to identify all possible vulnerabilities and weaknesses of the software resulting in information loss, adversely affecting revenue or reputation either insiders or external threat actors.

Static Testing is performed to check the defects in software without executing the code of the software application. Static testing is performed early on to avoid errors and fixing them is much easier. The errors that can’t not be found using Dynamic Testing, can be easily found by Static Testing.
Dynamic Testing is performed to analyze the dynamic behavior of the code. It is generally tested input values and output values for the expected behavior. The main purpose of dynamic testing is to test software behavior with dynamic variables or variables which are not constant and finding weak areas in software runtime environment. The code must be executed to test the dynamic behavior. It is mainly referred as validation.
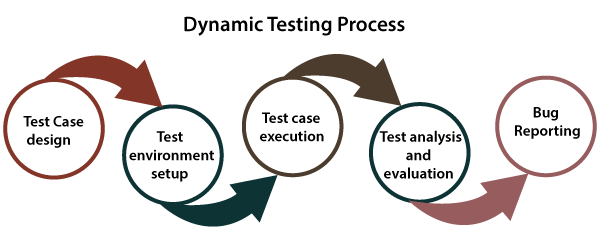
Network testing is to test security controls across a network to identify and demonstrate vulnerabilities and underlying risks. Network security testing is best identify to validate enterprise security defenses to meet compliance needs and help keep internal and external threat actors at bay.
We have a very well deployed technology center, managed, supported by qualified technical experts. It handles day-to-day activities to help organizations and IT departments focus on critical business applications and ensure continuous service.
At Security Operations Center (SOC) we are proactively monitoring and eliminating threats that impact your enterprise security. Real-time, comprehensive, and cost-effective analysis of endpoints, network. We completely rely on next generation cloud-based infrastructure to identify, remediate, and protect from any issues before they become disaster for enterprise.

VRM is the process of ensuring that the use of service providers and IT suppliers does not create an unacceptable potential for business disruption or a negative impact on business performance. VRM technology supports enterprises that must assess, monitor, and manage their risk exposure from third-party suppliers (TPSs) that provide IT products and services, or that have access to enterprise information – Gartner.
We can partner with you to drive your entire Cyber Security Compliance program right from inception to final compliance and maintaining this compliance year on year. We can help you prepare, manage and maintain any of the compliance requirements pertaining to any geo location specific needs or global compliance related to cyber security and privacy.


Security awareness training key to success of cyber security program in any enterprise. Most of the recent breaches have been caused due to human errors and training is essential for mitigating human error. We can tailor your training needs based on type of audiences be it end users, Sr Management, or technical support staff. Each one has different level of understanding and needs different set of training and awareness to meet today’s cyber security needs. We also support the training and awareness program with ongoing phishing campaigns